Tackling the digital divide is essential for your organization's prosperity in today's digital era. By recognizing the pitfalls of falling behind in digital transformation and implementing pragmatic measures to narrow the divide, you can secure your organization's growth and foster a more equitable digital environment.

The Microsoft Office Adoption Score functions as a crucial measurement for assessing your organization's utilization and adoption of Office 365 applications. By comprehending your present score and actively striving to boost adoption rates, you can tap into the complete capabilities of Office 365 tools, thereby amplifying your organization's productivity and effectiveness.

GPT-5 Is Just Around The Corner The rapid advancements in artificial intelligence (AI) have been nothing short of revolutionary, with the GPT-5 model set to bring further transformative changes. As businesses leverage these technologies for competitive advantage, it’s crucial to understand what GPT-5 entails and how it will impact the business landscape. In this in-depth...
In the ever-evolving realm of technology, businesses across numerous sectors have recognized the benefits of IT outsourcing to streamline their operations, bolster efficiency, and reduce expenses.
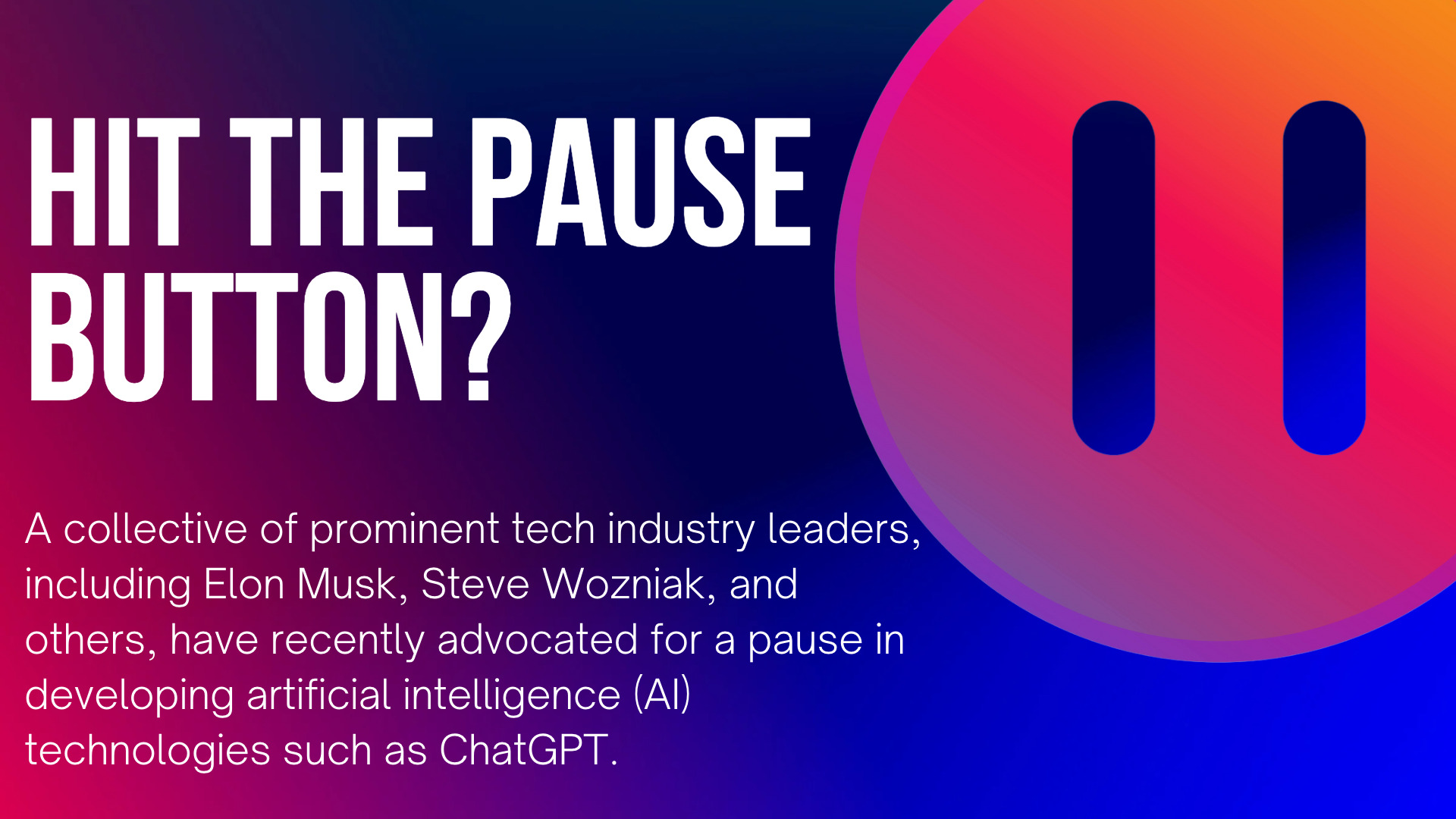
Emphasis on Addressing Ethical Concerns and Regulatory Oversight A collective of prominent tech industry leaders, including Elon Musk, Steve Wozniak, and others, have recently advocated for a pause in developing artificial intelligence (AI) technologies such as ChatGPT. Concerned by the swift advancements in AI, these visionaries emphasize the need to establish regulatory frameworks and carefully...

The Unrivaled Power of Browser Isolation in Defending Against Cyber Threats In an era where cyber threats are growing more sophisticated and prevalent, securing your online activity has become more critical than ever. One of the most effective ways to protect your digital identity and sensitive data is through browser isolation, a cutting-edge technology designed...

In the ever-changing landscape of digital threats, Dallas and Fort Worth businesses are making significant strides in bolstering their cybersecurity defenses.

Harnessing the Power of Microsoft Sentinel: Minimizing False Positives for a Robust Cybersecurity Strategy Microsoft Sentinel, a premier cloud-native Security Information and Event Management (SIEM) solution offers businesses cutting-edge cybersecurity features. This advanced system, designed for IT professionals and enterprise-level organizations, employs many tools and strategies for detecting threats in real time. However, despite its...

The Diverse Landscape of Network Security: Unlocking the Potential of a Safe Digital Future In today’s interconnected digital age, the importance of robust network security has never been greater. With the rise of sophisticated cyber threats and attacks, businesses, governments, and individuals must constantly stay ahead in their efforts to protect their digital assets. To...




